


|
Feature Article
Are your Sensitive Reports Really Secure?
By Dan Riehl - SecureMyi.com
We are often deeply concerned about data leaking from our production database to the outside world. We often focus a great deal of effort on securing these precious data jewels we call database files. But what about protecting the end result of these jewels — our printed reports? Our production reports consist of our precious data jewels, coordinated, manipulated, and cajoled into what becomes meaningful information in the form of a production report.
If we consider our database files to be sensitive, then our printed reports, which present that file data in a readable, organized format, must be protected with as much or, dare I say, more due diligence.
If your shop is like most, all, or almost all, Printer output queues are left unsecured. For some strange reason, we assign *JOBCTL special authority to our end users. The result of this *JOBCTL assignment is that they can view and manipulate the reports generated by others. This is usually the root of the problem of data leakage via printed reports. A user with *JOBCTL special authority can, with few exceptions, view and control any printed report on the system.
Perhaps to avoid the potential of a data leak through a printed report, we configure the user accounts with the command line restriction LMTCPB(*YES). As a further step, we don't present a menu option that allows them to view the spooled files of others. That's a nice solution, but there still can be alternative methods to view and leak the data in our sensitive reports. One such method is through the IBM i Navigator for Windows (a.k.a. Operations Navigator) Basic Operations tab.
IBM i Navigator for Windows - Basic Operations Tab
When we install IBM i Access for Windows, one of the pieces of the typical basic install is IBM i Navigator - Basic Operations. Basic Operations allows the user to view and send messages, work with printers, and work with their jobs and with their spooled files, listed as Printer Output). But many administrators do not know that when you right-click an item in Navigator (as in Printer Output), the user can select whose printer output to view. The shipped value is "Show only my own reports," but as you can see in the following figure, right-click shows a "Customize" option that further allows the user to "Include" reports for the users he or she chooses, or even "Include" the reports for ALL users.
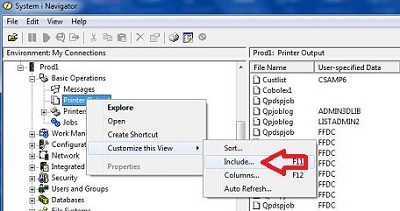
When "Include" is selected, the user can select from a plethora of options, as shown here. The user can even press the browse button to get a list of ALL the users on the system and select the reports for just those users that might have the data he or she is looking for (to leak).
Read More . .
|

Security Related News for IBM i
PowerTech Network Security 6.50 Announced
PowerTech, a division of HelpSystems, has announced the release of a new version of their Network Security exit program solution. Network Security 6.50 introduces a browser interface that helps improve visibility of transactions occurring on the system.
The new browser interface provides productivity enhancements, reducing the time spent in setting security rules. Read the 6.50 Press Release
Live Security Related Webcasts and Training for IBM i
October Events
Part-Time Privileges: Accountability for Powerful Users
Live Webcast - Presented by Powertech
Wednesday, Oct 22 1:00pm CT
More Information and Register to Attend
COMMON 2014 Fall Conference & Expo
Oct 27 - 29
Hyatt Regency Indianapolis • Indianapolis, Indiana
More Information and Register to Attend
Coffee with Carol: Configuring iAccess Servers to use SSL
with Carol Woodbury
Live Webcast - Presented by Skyview Partners
Wednesday, Oct 29 10:00am CDT
More Information and Register to Attend
November Events
Live Hands-On - Security Audit and Vulnerability Assessment Workshop
for IBM i, iSeries AS/400 with Dan Riehl
Training Workshop - Nov 11-14 - Presented by The 400 School, Inc.
Dan Riehl presents this 4-Day Live Online Hands-on Workshop.
More Information and Register to Attend
Live Hands-On - IBM i, iSeries System Administration and Control Workshop
with Dan Riehl
Training Workshop - Nov 17-21 - Presented by The 400 School, Inc.
Dan Riehl presents this 5-Day Live Online Hands-on Workshop.
More Information and Register to Attend
|


|
Security Shorts
Are You Saving QAUDJRN Journal Receivers
By Dan Riehl - SecureMyi.com
If you are auditing security-related events using the QAUDJRN journal, make sure you save the QAUDJRN journal receivers before deleting them. These are often needed when researching security events that have occurred on your system. If you delete the journal receivers before they are saved, your ability to track down changes to the system is severely degraded.
The journal receivers for QAUDJRN should be created in a library that is included in your backup plan. Do not create the QAUDJRN journal receivers in library QSYS, unless you use special processing to save these critical journal receivers.
Special handling of saving the QAUDJRN journal receivers, assuming the receivers reside in QSYS and start with the characters AUDRCV, could look like the following:
SAVOBJ OBJ(AUDJRN*) LIB(QSYS) DEV(TAP01) OBJTYPE(*JRNRCV)
If the receivers reside in a library other than QSYS, you can use your normal backup processes to save the entire library (AUDLIB), including all the journal receivers using the command:
SAVLIB LIB(AUDLIB) DEV(TAP01)
For a full backup, make sure to back up your QAUDJRN journal receivers.
|
Sponsored Links
IT Security and Compliance Group
In Depth Security Assessment of IBM i
Upgrade to QSECURITY level 40 or 50
Forensic Research and Analysis
Audit Assistance and Remediation
Security Training for IT and Audit Staff
Software Selection & Configuration
Security and Systems Programming
Customized IBM i (AS/400) Training -
Presented Live at your offices
Live Online Hands-On Workshops
|
















