
|
||
|
John Earl Memorial Tribute - January 9, 2013 - Vol 3, Issue 21
|
||

|
||
John's Celebration of LifeJohn's Celebration of Life is being held
Sunday, January 13th, 1:30 PM PST at For those desiring to contribte with gifts or donations, please see the information below on the John Earl Memorial Fund "And God shall wipe away all tears from their eyes; and there shall be no more death, neither sorrow, nor crying, neither shall there be any more pain: for the former things are passed away." Revelation 21:4 KJV Tribute to JohnFrom Carol Woodbury I will remember John for his passion. His passion for the IBM i – and of course, for his passion for security. I will also remember John as a gifted presenter and writer. He was incredibly articulate with both speech and the pen. And while John had a serious side, no doubt, John also loved life. I remember him sticking his head into the back of my session room at COMMON while I was presenting, he was making faces at me. And could HE tell a joke! The funny thing is that he got as tickled at the joke as his audience so by the end, he was laughing as hard at the joke as everyone else. He also loved wrestling and I knew I had a special ‘in’ with him when he found out I had graduated from same the high school as one of his wrestling idles, Dan Gable. (That, and I knew what a ‘half-Nelson’ was and what it meant to ‘pin’ your opponent!) But most of all, I will remember John’s passion for his family and his infectious smile. Unfortunately John’s passion has been taken from us but his legacy will live on for a long, long time. The prayers of SkyView Partners are with John’s wife, Kathy and the entire Earl family. 
|
Feature Article
Tracking QSECOFR with the IBM Security APIs(Swap Profile)
By John EarlThis article first appeared in the book "PowerTips for OS/400 Security" Reader Question:In our shop we have several people who need to use the QSECOFR user profile, but I have a problem trying to figure out who makes which changes as the security officer. Is there any way to reliably track who was signed on as the security officer when a change happened? John's Answer:Yes. In fact there are many. But first, let me commend you for not giving *ALLOBJ and other special authorities to your programmers all of the time. It's simply too dangerous to allow someone to operate on a daily basis with the i/OS equivalent of a nuclear missile strapped to his hip. Let me also suggest that you not give the QSECOFR password to your programmers or anyone in your shop for that matter. It is better to create a QSECOFR clone (you can call it ZSECOFR) and give the programmers the ability to use that profile for emergency work. I like the QSECOFR clone idea because you are less likely of getting the QSECOFR profile corrupted, broken, disabled, or otherwise unusable. An alternate security officer can have all of the power of QSECOFR but still leave the QSECOFR profile available for those critical emergencies when nothing else will work. As an added precaution, you might even choose to give the alternate security officer profile slightly less authority than QSECOFR typically carries (remove *SERVICE and *AUDIT for example), yet still allow it to function successfully as an emergency profile. More from John on Tracking Security OfficersTo answer your original question about tracking who is using that powerful profile, allow me to point you towards a solution that I have used successfully for some time. The solution uses the Get Profile Handle and Set Profile APIs to perform password validation and profile swapping for a user who you want to assume the authority of a security officer. To implement this solution, create user profile ZSECOFR as a clone of QSECOFR. For safety purposes, remove *AUDIT and *SERVICE special authority, because they offer the ability to change things, such as disk configurations and object auditing, that you might not want changed as a matter of normal application recovery. Don't assign a password to ZSECOFR, and set the initial program to *NONE and the initial menu to *SIGNOFF because you don't ever want anyone to sign on directly as that profile. The create command for the ZSECOFR user profile might look like this:
CRTUSRPRF USRPRF(ZSECOFR) PASSWORD(*NONE) +
USRCLS(*SECOFR) INLMNU(*SIGNOFF) +
TEXT('Alternate Security Officer') +
SPCAUT(*ALLOBJ *IOSYSCFG *JOBCTL +
*SAVSYS *SECADM *SPLCTL)
For good measure, you can also turn on auditing for the user ZSECOFR so that everything that is done by this user is logged to the QAUDJRN security-auditing journal as well. The command to accomplish user profile auditing might look like this:
CHGUSRAUD USRPRF(ZSECOFR) +
OBJAUD(*ALL) +
AUDLVL(*CMD *CREATE *DELETE *OBJMGT *SAVRST *SECURITY +
*SERVICE *SYSMGT)
Now you need a program that will allow your programmers to assume ZSECOFR's identity. In this case, you're going to use the profile swapping APIs rather than the usual method of adopting authority, because you want a clear audit trail whenever someone uses ZSECOFR authority. Program SWPUSRPRF shown below uses three of the user profile APIs to accomplish this. The first API, QSYGETPH, accepts the user profile name and the valid password for the user profile you want to become. After QSYGETPH validates authority, it returns a twelve-character hexadecimal profile handle that can be passed to the second API, QWTSETP. QWTSETP actually performs the profile swap and changes the authority and current user of the job, and, finally, the QSYRLSPH API does the housekeeping by releasing the profile handle. For security purposes, the profile handle that QSYGETPH provides is limited for use only in the job that it was created in. This precaution prevents someone from creating a profile handle in one job and then distributing it to other processes or saving a profile handle for clandestine use on another day. Is There A Security Hole Here?Read More of John Earl's Great article and get His Source Code to Swap Users. |
|
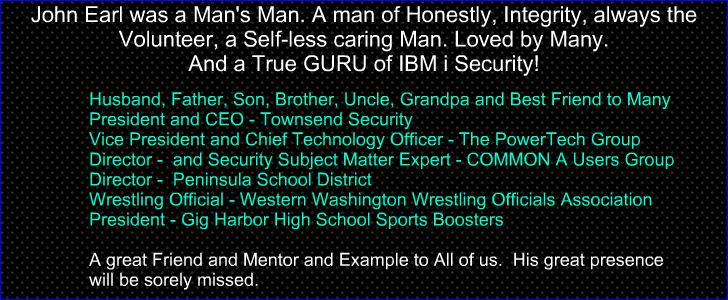
Our Great Memories of John EarlJohn transformed PowerTech from a consulting company to a Software company. He was a computer geek that had the ability to communicate. He became the evangelist for exit point security and he taught me (and others) how to be evangelists too. I remember in 1999, when John was patiently going over exit points and the use of ODBC, FTP and Remote Command. He wanted me to learn about exit points so that I could help to sell PowerLock. I was frustrated that I was not getting some concept and John very calmly told me, “David, don’t worry about it. Not very many people understand this exit point problem. You just have to be one lesson ahead of the people you are talking with. Remember, in the land of the blind the one eyed man is king.” And then he gave me that John Earl smile. His infectious smile that would melt away everything and cause you to join him in that moment of celebration. He had that Chuck Yeagar factor. Anytime a customer would ask an impossible question or the sales team wanted some crazy feature. John would take over in his calm way, not make any assumptions and start asking questions. He had a way of calming down any situation and making you feel like everything was under control. “Oh, don’t worry, we can get that done over the weekend,’ was a common refrain from John, and you believed him, until he would add, “I didn’t say which weekend.” And there he was again, pulling you in. John was a great public speaker, but he enrolled in “Toastmaster’s” a few years ago to get better. He was a great wrestler, and he joined the “Old Timer’s Tournament”. Yes, really, in his late 40s he joins the “Old Timers Tournament”. He was 260 pounds wrestling 320+ pound guys and complaining about how big they were. I thought he must be doing this to improve himself. I was impressed that he would continue to work on his wrestling after so many years. I asked him why he was doing it. He told me, “It is easier than dieting and it makes me feel just as skinny as if I lost 50 or 60 pounds.” 
As PowerTech grew, we hired more and more people. And John would patiently help train the new people. Inevitably, someone would ask John. What is 5250 anyway? And John would reply, “It is the average age and weight of an AS400 programmer.” I loved John Earl and I had many occasions to tell him that and give him a big hug. Unfortunately, as we got older, we would only see each other a few times a year, but it was always good to see him and talk with him. He taught me many things. He loved to have philosophical discussions and to argue about issues. Often taking the opposite side of an argument to test it and see if we could reach a better answer. It could be about anything. In the weeks approaching his departure from this world, I had the opportunity to visit him a few times. He was laying in his bed and was not real mobile. He had lost the ability to read, which I am sure was one of the most painful things for him. And he would speak slowly. Kathy was just starting to get him some books on tape. So, as I sat there in his room with his 21 year old son by my side. It was hard to tell if John was really in there. This was not the John I knew. His eyes were opening and closing. In an effort to cheer him up I said, “John I hear you are getting some books on tape. I was thinking of getting you “50 shades of Gray”. I was thinking you might enjoy that.” John’s eyes opened and he turned toward me - - recognition. I had reached him. And quietly, slowly he says, “David , you’re 50 shades of a__hole.” And I saw the faintest hint of his smile. Michael and I laughed. I love John Earl. David O'Neal - Former President - PowerTechJohn was bigger than life and there are a lot of stories about him. One of my favorites is the origins of the PowerTech Group. As it was told to me, John was responsible for computer security at a large IBM i retail company when there was a disaster in General Ledger processing. After the forensics were performed it was discovered that the GL chart of accounts contained a tiny subset of the accounts that should have there, and most postings were going into accounting oblivion because there wasn’t anything to post to. Further forensics identified the problem: a senior accounting executive had downloaded the chart of accounts to their PC and taken it home over the weekend. They deleted the accounts they didn’t need to work with, made changes to the ones they did, and then uploaded the changes back to the IBM i on Monday when they returned to work. Unfortunately, they did a replace when they did the upload so most of the posting accounts were wiped out and chaos reigned when night processing took place. John recognized there was a solution to controlling this and put a team together that used the TCP/IP and Host Server exit points to control network traffic. That was the origin of ‘PowerLock’ which was the network control exit point product that the PowerTech Group used to grow into the premier security vendor in the industry. I will miss John very much. Nick Blattner - Friend and CoWorkerI had the pleasure of working with John at PowerTech for ten years. There are many memories that range from the sounds coming from above of wrestling in the hallway on the second floor of our offices to John's concepts of how to secure applications. But what impressed me most was his insistence that customers should understand the right way to secure systems and applications. Proper attention should be given to object security and to the authorities and the 'special authorities' assigned to users. We built and sold network exit point security solutions, but I never heard John speak of that product as the 'right' way to do things. Instead, it was only an aid to those who couldn't set the resources aside to do it the right way. Systems that were properly secured didn't need the product. We couldn't sell into businesses with those systems. John understood system and application security, but he also understood the reality faced by our customers. We could tell customers how we could help them with our products, but we could and should also explain what truly ought to be done. The support for 'doing the right thing' is a characteristic of management authority that's hard to find in business. I have memories of John that I'm glad to have. To me, though, John will always symbolize 'the right way'. Tom Liotta - Friend and CoWorkerWhen you pick up a book you often times flip it over and you find notes about the author. Sometimes these notes talk about the person’s educational background, work experience and expertise. If John Earl had written a book the back cover might not seem impressive, after all his expertise was in computer security, I mean how boring is that? Yet to dismiss John by simply reading the cover was to miss a truly great man. John Earl knew that most people in our IBMi community don’t like to talk about security. There is some sort of fear or complacency about it, I’m not sure which. Yet John was a student of it, learned his subject well, engage people with a smile and a passion unmatched by most, and made security a lot less daunting than it seemed. I recall visiting a customer with John once. The customer was located in Utah. From the first time we met for dinner, John engaged them. He talked calmly. He demonstrated that he knew what he was talking about. I simply watched and played a bit of a muse to John as he told the customer that we could help him. The next day on location, John looked at the customer and told him what he needed to do. I remember the customer stopping and saying something like “If I do that won’t this happen?” John smiled and assured him that would not be the case and guided him through a security exercise that was eye opening and had none of the perceived ramifications the customer thought. That was vintage John Earl. Engaging, passionate, involved and focused on serving. When I reflect on John’s life and his contribution to our IBMi community, these characteristics stand out. Over the few years I worked with John I realized that this wasn’t just his “work” persona, that this was also how he lived his personal life. Whether it was wrestling that he coached, or COMMON , or the local technical college he served at, he was involved, engaging and passionate. There are so few people we meet that once you’ve done so you consider it pure joy to know them. John Earl was one of those people. Did we always agree? No. But because of his passion for whatever subject, I completely respected his viewpoint and learned a lot along the way. Later in his life our paths did not cross as often as they should have, but when I did happen to run across him at a tradeshow or at the airport, there was always that smile and laugh that put you at ease and just made the world a little brighter that day. To John, though he is no longer with us, his family is and they can take comfort in the fact that John lived his time on this earth well and served people. Rest in peace. John Vanderwall – Skyview PartnersBelow is a photo that hangs proudly in our halls at Townsend Security. It truly captures the spirit that John brought to our company. We are sorry to tell you that our friend and former CEO, John Earl, passed away on January 3rd after a long struggle with cancer. John was a loving husband and father, a mentor, and a strong supporter of our community. Our thoughts and prayers are with John's wife Kathy and the entire Earl Family. Townsend Security
We are all deeply saddened by the passing of John Earl. On the occasions when we met with John, for example at Common Conferences, or spoke with him on the phone, John proved to be an excellent listener whose ideas and sound advice were sincerely appreciated. John’s passing will be felt not only by his family but by the professional community as a whole. Eli Spitz - Raz-Lee SecurityView MCPressOnline.com Tribute to John EarlView IT Jungle Tribute to John Earl |
||

|
||
|
||
John Earl Web Links
|
Favorite John Earl Quotes
|

|
Security Shorts - Where Does *PUBLIC Get All That Authority?By John Earl This article appeared in the book Powertips for OS/400 Security, Reader QuestionI recently went back to work for a former employer after a four-year absence. When I worked here in the '90s, everything was very secure, but now it seems like *PUBLIC has authority to everything. The system administrator I replaced just didn't care about security. Now I'm noticing that every new system moved into production gives *PUBLIC *ALL authority. How can I stop this? John's AnswerThe situation you describe is more the rule than the exception. As I review security for i/OS shops, I find it is common that *PUBLIC has *CHANGE or *ALL authority to large numbers of application objects. If *PUBLIC has too much authority in your shop, you should review your system settings to reign in this excessive level of public authority. First, let's review how *PUBLIC receives authority to new objects. With every create command (CRTPF, CRTJOBD, CRTCLPGM--all those commands that begin with the prefix CRT), there is a *PUBLIC Authority (AUT) parameter. This parameter tells each create command what authority *PUBLIC should have to these newly created objects. The default value for all of these commands is something called Library Create Authority (*LIBCRTAUT), however, the person who creates the new object can specify that *PUBLIC should have *ALL, *USE, *CHANGE, or even *EXCLUDE authority. Regardless of which authority level is chosen, *PUBLIC will be granted that authority. If the person who creates the object neglects to choose a specific authority for *PUBLIC, all of the create commands will revert to the default value of *LIBCRTAUT – which means “Go ask the library description what authority *PUBLIC will have to this new object”. Every library description has a default *PUBLIC authority parameter, called Create Authority (CRTAUT). This value is used to determine what authority *PUBLIC will get to new objects that are created in this library when the AUT parameter on the CRT command is left unchanged as “*LIBCRTAUT”. You can run the Display Library Description (DSPLIBD) command for any library, and the library header description will show you the Create Authority for that library. The valid values include *ALL, *USE, *CHANGE, and *EXCLUDE. The other valid value, and the one most often used, is *SYSVAL. This value tells new objects to look to the system value QCRTAUT to determine what authority *PUBLIC should have to those new objects. Most libraries on your system are probably set to this default *SYSVAL value. Unfortunately for security-conscious System i shops, the IBM shipped default for system value QCRTAUT is *CHANGE. This means that, on most System i machines, when a new object is created, the create command defers to the library description and the library description defers to the system value, which is set as *CHANGE. So on most systems, *PUBLIC ends up with *CHANGE authority to all new objects. A good rule of thumb is that users need no more than *USE authority to programs and usually no more than *CHANGE authority to data, so the CRTAUT value on the library could be set to *USE for libraries containing programs and *CHANGE to libraries containing files--at least until you can implement a more comprehensive solution. |
||