


|
Feature Article
Do you Every Really Logoff? IBM i Access - CWBLOGON
By Dan Riehl - SecureMyi.com
Most of us run IBM i Access for Windows. Some run the Windows 10 replacement software, IBM Access Client Solutions. You most likely use the Personal Communications Telnet 5250 emulation software to provide your Text-Based workstation access. You may also use IBM i Navigator (Operations Navigator, iSeries Navigator).
There are several IBM supplied applications that are installed on your PC when you install IBM i Access for Windows. Included in these additional applications are the Remote Command client, the ODBC Driver and various File Transfer programs and Service utilities. One critical piece of software that is installed is the command interface to Set or Flush the Signon Server cached User IDs and Passwords, which is the topic of our discussion here.
When you run IBM i Access functions on your PC that require communications with the host, you must first authenticate to the host. To accomplish this authentication, IBM provides the Signon Server GUI window where you provide your credentials(i.e. UserID and Password) as shown here.
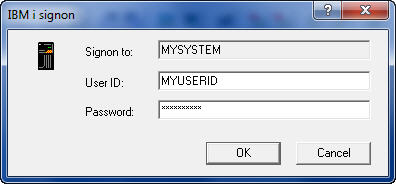
Once you have successfully authenticated, your PC provides an open pipe to access the IBM i without any further authentication. You can transfer files, run remote commands, examine spooled files, etc.
So, do you shut down your PC, or Flush your credentials when you leave your desk? Or do your leave the pipe open for anyone that happens to wander by your unattended workstation?
When you enter your User ID and Password when prompted, they are passed to the IBM i Signon Server, or other service, and also cached on your PC for later use. Once the authentication information is cached on your PC, you do not need to supply the information again, until you reboot your PC (depending on your configuration.)
So, when you now need to run a remote command, or access a database using ODBC, or download a file with File Transfer, or view a spooled file, you are not required to manually authenticate again. The cached User ID and Password for that system can be automatically supplied to the service requested without any user action required. This is both a blessing and a curse. It's a blessing because you are not required to manually log-on for each action you want to initiate. It's a curse because your credentials are cached on your PC and can be used by anyone who can access your workstation. What you have, in essence is an "open pipe" to the system, using YOUR credentials.
Even if you select the IBM i Access Log-on option to "Prompt Every Time", I have found that some services do not "Prompt Every Time." They instead use your cached credentials.
From a security perspective, this caching of User ID and Passwords on the local PC and having an "open pipe" to the host present exposures that need to be addressed.
Click - to Read the Entire Article for the details
|

Live Security Related Webcasts and Training for IBM i
August Events
Live Hands-On - IBM i, iSeries Programming Introduction Workshop
with Dan Riehl
Training Workshop - August 20-24 - Presented by The 400 School, Inc.
Dan Riehl presents this 5-Day Live Online Hands-on Workshop.
More Information and Register to Attend
Live Hands-On - Expanded Control Language Programming Workshop
with Dan Riehl
Training Workshop - August 27 - 31 - Presented by The 400 School, Inc.
Dan Riehl presents this 5-Day Live Online Hands-on Workshop.
More Information and Register to Attend
September Events
Live Hands-On - Introduction to ILE RPG IV Programming Workshop
with Dan Riehl
Training Workshop - September 10-14 - Presented by The 400 School, Inc.
Dan Riehl presents this 4-Day Live Online Hands-on Workshop.
More Information and Register to Attend
Live Hands-On - IBM i, iSeries System Operations Workshop
with Dan Riehl
Training Workshop - September 22-24 - Presented by The 400 School, Inc.
Dan Riehl presents this 3-Day Live Online Hands-on Workshop.
More Information and Register to Attend
Live Hands-On - IBM i, iSeries Expanded System Operations Workshop
with Dan Riehl
Training Workshop - September 22-28 - Presented by The 400 School, Inc.
Dan Riehl presents this 5-Day Live Online Hands-on Workshop.
More Information and Register to Attend
October Events
Live Hands-On - IBM i, iSeries System Administration and Control Workshop
with Dan Riehl
Training Workshop - October 1 - 5 - Presented by The 400 School, Inc.
Dan Riehl presents this 5-Day Live Online Hands-on Workshop.
More Information and Register to Attend
Live Hands-On - IBM i, iSeries Expanded Security Workshop
with Dan Riehl
Training Workshop - October 9 - 12 - Presented by The 400 School, Inc.
Dan Riehl presents this 4-Day Live Online Hands-on Workshop.
More Information and Register to Attend
|



|
Security Shorts
Security Shorts
Auditing Newly Created Objects
By Dan Riehl - SecureMyi.com
The IBM i has excellent built-in auditing capabilities. You can audit various types of important events, you can audit object access, and you can audit access to IFS "Objects". I have used the object auditing facilities quite heavily. But, when I was asked the question "How do you turn on auditing for newly created files and directories in the IFS?" I knew that there was a way to do this, but the method did not come readily to mind for IFS "Objects". After searching the web and performing quite a lot of testing, I happily now have the answer to that question. I hope that the information will be helpful to you.
Auditing Newly Created QSYS.LIB Objects
The System value QCRTOBJAUD specifies the global default value for the auditing level specified for newly created objects. The shipped value is *NONE, meaning, newly created objects will not be audited at the global/system level. You can override the QCRTOBJAUD system value at the library level by specifying the CRTOBJAUD parameter of the CRTLIB(Create Library) and CHGLIB(Change Library) command as shown here.
CHGLIB LIB(MYLIB) CRTOBJAUD(*CHANGE)
When a library is created, the default value for the CRTLIB's CRTOBJAUD parameter is *SYSVAL, but can be set as desired to *ALL, *CHANGE, *USRPRF, *NONE or *SYSVAL.
CRTLIB LIB(MYLIB) . . CRTOBJAUD(*CHANGE)
So, now, whenever a new object is created in MYLIB, the object's OBJAUD value will automatically be set to *CHANGE.
Auditing Newly Created IFS "Objects"
The IFS /root file system is used to store various types of files, directories, folders and documents. Often sensitive data is stored there in MS/Excel spreadsheets, Word documents, images, audio, pdf reports, and many other types of files.
In addition to being the global setting for the QSYS.LIB file system, the system value QCRTOBJAUD is also the global setting applied to IFS directories. If you want to turn on auditing for all newly created IFS "objects", you set the system value QCRTOBJAUD as required to *ALL, *CHANGE or *USRPRF. Within the IFS, this global setting can be overridden at the directory level using the CHGATR(Change Attribute) command as shown here.
CHGATR OBJ('home/myuser') ATR(*CRTOBJAUD) VALUE(*CHANGE)
If you want the *CRTOBJAUD auditing attribute to be applied to subdirectories also, include the SUBTREE(*ALL) option of the CHGATR command.
So, the key to managing auditing for newly created objects in the IFS is the QCRTOBJAUD System Value when used in conjunction with the CHGATR command.
With the CHGATR command, you specify the *CRTOBJAUD attribute and corresponding value for the selected IFS directory, and the associated sub-directories.
|
Sponsored Links

IT Security and Compliance Group
- In Depth Security Assessment of IBM i
- Upgrade to QSECURITY level 40
- Forensic Research and Analysis
- Audit Assistance and Remediation
- Security Training for IT and Audit Staff
- Software Selection & Configuration
- Security and Systems Programming
- General Security and System Assistance

Customized IBM i (iSeries, AS/400) Training -
Presented Live at your offices
LIVE Online Hands-On Workshops
- ILE RPG IV Programming
- RPG/400 and RPG III Programming
- ILE COBOL/400 Programming
- Interactive Programming Workshops
- System Operations Workshops
- System Administration and Control
- Security and Auditing Workshops
- Control Language Programming
- IBM i Concepts and Facilities
- Query Workshop

|





















